With the widespread attention, and potential applications of blockchain and artificial intelligence technologies, the privacy protection techniques that arise as a direct result of integration of the two technologies is gaining notable significance. These privacy protection techniques not only protect the privacy of individuals, but they also guarantee the dependability and security of the data.
In this article, we will be talking about how the collaboration between AI and blockchain gives birth to numerous privacy protection techniques, and their application in different verticals including de-identification, data encryption, k-anonymity, and multi-tier distributed ledger methods. Furthermore, we will also try to analyze the deficiencies along with their actual cause, and offer solutions accordingly.
The blockchain network was first introduced to the world when in 2008 Nakamoto introduced Bitcoin, a cryptocurrency built on the blockchain network. Ever since its introduction, blockchain has gained a lot of popularity, especially in the past few years. The value at which Bitcoin is trading today, and it crossing the Trillion-dollar market cap mark indicates that blockchain has the potential to generate substantial revenue and profits for the industry.
Blockchain technology can be categorized primarily on the basis of the level of accessibility and control they offer, with Public, Private, and Federated being the three main types of blockchain technologies. Popular cryptocurrencies and blockchain architectures like Bitcoin and Ethereum are public blockchain offerings as they are decentralized in nature, and they allow nodes to enter or exit the network freely, and thus promotes maximum decentralization.
The following figure depicts the structure of Ethereum as it utilizes a linked list to establish connections between different blocks. The header of the block stores the hash address of the preceding block in order to establish a linkage between the two successive blocks.
The development, and implementation of the blockchain technology is followed with legitimate security and privacy concerns in various fields that cannot be neglected. For example, a data breach in the financial industry can result in heavy losses, while a breach in military or healthcare systems can be disastrous. To prevent these scenarios, protection of data, user assets, and identity information has been a major focus of the blockchain security research community, as to ensure the development of the blockchain technology, it is essential to maintain its security.
Ethereum is a decentralized blockchain platform that upholds a shared ledger of information collaboratively using multiple nodes. Each node in the Ethereum network makes use of the EVM or Ethereum Vector Machine to compile smart contracts, and facilitate the communication between nodes that occur via a P2P or peer-to-peer network. Each node on the Ethereum network is provided with unique functions, and permissions, although all the nodes can be used for gathering transactions, and engaging in block mining. Furthermore, it is worth noting that when compared to Bitcoin, Ethereum displays faster block generation speeds with a lead of nearly 15 seconds. It means that crypto miners have a better chance at acquiring rewards quicker while the interval time for verifying transactions is reduced significantly.
On the other hand, AI or Artificial Intelligence is a branch in modern science that focuses on developing machines that are capable of decision-making, and can simulate autonomous thinking comparable to a human’s ability. Artificial Intelligence is a very vast branch in itself with numerous subfields including deep learning, computer vision, natural language processing, and more. NLP in particular has been a subfield that has been focussed heavily in the past few years that has resulted in the development of some top-notch LLMs like GPT and BERT. NLP is headed towards near perfection, and the final step of NLP is processing text transformations that can make computers understandable, and recent models like ChatGPT built on GPT-4 indicated that the research is headed towards the right direction.
Another subfield that is quite popular amongst AI developers is deep learning, an AI technique that works by imitating the structure of neurons. In a conventional deep learning framework, the external input information is processed layer by layer by training hierarchical network structures, and it is then passed on to a hidden layer for final representation. Deep learning frameworks can be classified into two categories: Supervised learning, and Unsupervised learning.

The above image depicts the architecture of deep learning perceptron, and as it can be seen in the image, a deep learning framework employs a multiple-level neural network architecture to learn the features in the data. The neural network consists of three types of layers including the hidden layer, the input payer, and the output layer. Each perceptron layer in the framework is connected to the next layer in order to form a deep learning framework.
Finally, we have the integration of blockchain and artificial intelligence technologies as these two technologies are being applied across different industries and domains with an increase in the concern regarding cybersecurity, data security, and privacy protection. Applications that aim to integrate blockchain and artificial intelligence manifest the integration in the following aspects.
- Utilizing blockchain technology to record and store the training data, input and output of the models, and parameters, ensuring accountability, and transparency in model audits.
- Using blockchain frameworks to deploy AI models to achieve decentralization services among models, and enhancing the scalability and stability of the system.
- Providing secure access to external AI data and models using decentralized systems, and enabling blockchain networks to acquire external information that is reliable.
- Using blockchain-based token designs and incentive mechanisms to establish connections and trust-worthy interactions between users and AI model developers.
Privacy Protection Through the Integration of Blockchain and AI Technologies
In the current scenario, data trust systems have certain limitations that compromise the reliability of the data transmission. To challenge these limitations, blockchain technologies can be deployed to establish a dependable and secure data sharing & storage solution that offers privacy protection, and enhances data security. Some of the applications of blockchain in AI privacy protection are mentioned in the following table.
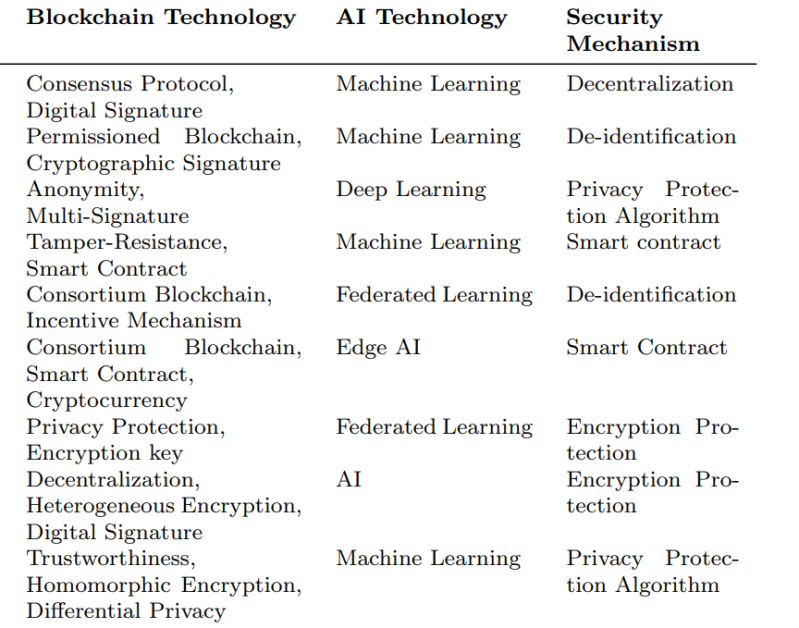
By enhancing the implementation & integration of these technologies, the protective capacity & security of current data trust systems can be boosted significantly.
Data Encryption
Traditionally, data sharing and data storing methods have been vulnerable to security threats because they are dependent on centralized servers that makes them an easily identifiable target for attackers. The vulnerability of these methods gives rise to serious complications such as data tampering, and data leaks, and given the current security requirements, encryption methods alone are not sufficient to ensure the safety & security of the data, which is the main reason behind the emergence of privacy protection technologies based on the integration of artificial intelligence & blockchain.
Let’s have a look at a blockchain-based privacy preserving federated learning scheme that aims to improve the Multi-Krum technique, and combine it with homomorphic encryption to achieve ciphertext-level model filtering and model aggregation that can verify local models while maintaining privacy protection. The Paillier homomorphic encryption technique is used in this method to encrypt model updates, and thus providing additional privacy protection. The Paillier algorithm works as depicted.

De-Identification
De-Identification is a method that is commonly used to anonymize personal identification information of a user in the data by separating the data from the data identifiers, and thus reducing the risk of data tracking. There exists a decentralized AI framework built on permissioned blockchain technology that uses the above mentioned approach. The AI framework essentially separates the personal identification information from non-personal information effectively, and then stores the hash values of the personal identification information in the blockchain network. The proposed AI framework can be utilized in the medical industry to share medical records & information of a patient without revealing his/her true identity. As depicted in the following image, the proposed AI framework uses two independent blockchain for data requests with one blockchain network storing the patient’s information along with data access permissions whereas the second blockchain network captures audit traces of any requests or queries made by requesters. As a result, patients still have complete authority and control over their medical records & sensitive information while enabling secure & safe data sharing within multiple entities on the network.
Multi-Layered Distributed Ledger
A multi-layered distributed ledger is a data storage system with decentralization property and multiple hierarchical layers that are designed to maximize efficiency, and secure the data sharing process along with enhanced privacy protection. DeepLinQ is a blockchain-based multi-layered decentralized distributed ledger that addresses a user’s concern regarding data privacy & data sharing by enabling privacy-protected data privacy. DeepLinQ archives the promised data privacy by employing various techniques like on-demand querying, access control, proxy reservation, and smart contracts to leverage blockchain network’s characteristics including consensus mechanism, complete decentralization, and anonymity to protect data privacy.
K-Anonymity
The K-Anonymity method is a privacy protection method that aims to target & group individuals in a dataset in a way that every group has at least K individuals with identical attribute values, and therefore protecting the identity & privacy of individual users. The K-Anonymity method has been the basis of a proposed reliable transactional model that facilitates transactions between energy nodes, and electric vehicles. In this model, the K-Anonymity method serves two functions: first, it hides the location of the EVs by constructing a unified request using K-Anonymity techniques that conceal or hide the location of the owner of the car; second, the K-Anonymity method conceals user identifiers so that attackers are not left with the option to link users to their electric vehicles.
Evaluation and Situation Analysis
In this section, we will be talking about comprehensive analysis and evaluation of ten privacy protection systems using the fusion of blockchain and AI technologies that have been proposed in recent years. The evaluation focuses on five major characteristics of these proposed methods including: authority management, data protection, access control, scalability and network security, and also discusses the strengths, weaknesses, and potential areas of improvement. It’s the unique features resulting from the integration of AI and blockchain technologies that have paved ways for new ideas, and solutions for enhanced privacy protection. For reference, the image below shows different evaluation metrics employed to derive the analytical results for the combined application of the blockchain and AI technologies.

Authority Management
Access control is a security & privacy technology that is used to restrict a user’s access to authorized resources on the basis of pre-defined rules, set of instructions, policies, safeguarding data integrity, and system security. There exists an intelligent privacy parking management system that makes use of a Role-Based Access Control or RBAC model to manage permissions. In the framework, each user is assigned one or more roles, and are then classified according to roles that allows the system to control attribute access permissions. Users on the network can make use of their blockchain address to verify their identity, and get attribute authorization access.
Access Control
Access control is one of the key fundamentals of privacy protection, restricting access based on group membership & user identity to ensure that it is only the authorized users who can access specific resources that they are allowed to access, and thus protecting the system from unwanted to forced access. To ensure effective and efficient access control, the framework needs to consider multiple factors including authorization, user authentication, and access policies.
Digital Identity Technology is an emerging approach for IoT applications that can provide safe & secure access control, and ensure data & device privacy. The method proposes to use a series of access control policies that are based on cryptographic primitives, and digital identity technology or DIT to protect the security of communications between entities such as drones, cloud servers, and Ground Station Servers (GSS). Once the registration of the entity is completed, credentials are stored in the memory. The table included below summarizes the types of defects in the framework.

Data Protection
Data protection is used to refer to measures including data encryption, access control, security auditing, and data backup to ensure that the data of a user is not accessed illegally, tampered with, or leaked. When it comes to data processing, technologies like data masking, anonymization, data isolation, and data encryption can be used to protect data from unauthorized access, and leakage. Furthermore, encryption technologies such as homomorphic encryption, differential privacy protection, digital signature algorithms, asymmetric encryption algorithms, and hash algorithms, can prevent unauthorized & illegal access by non-authorized users and ensure data confidentiality.
Network Security
Network security is a broad field that encompasses different aspects including ensuring data confidentiality & integrity, preventing network attacks, and protecting the system from network viruses & malicious software. To ensure the safety, reliability, and security of the system, a series of secure network architectures and protocols, and security measures need to be adopted. Furthermore, analyzing and assessing various network threats and coming up with corresponding defense mechanisms and security strategies are essential to improve the reliability & security of the system.

Scalability
Scalability refers to a system’s ability to handle larger amounts of data or an increasing number of users. When designing a scalable system, developers must consider system performance, data storage, node management, transmission, and several other factors. Furthermore, when ensuring the scalability of a framework or a system, developers must take into account the system security to prevent data breaches, data leaks, and other security risks.
Developers have designed a system in compliance with European General Data Protection Rules or GDPR by storing privacy-related information, and artwork metadata in a distributed file system that exists off the chain. Artwork metadata and digital tokens are stored in OrbitDB, a database storage system that uses multiple nodes to store the data, and thus ensures data security & privacy. The off-chain distributed system disperses data storage, and thus improves the scalability of the system.

Situation Analysis
The amalgamation of AI and blockchain technologies has resulted in developing a system that focuses heavily on protecting the privacy, identity, and data of the users. Although AI data privacy systems still face some challenges like network security, data protection, scalability, and access control, it is crucial to consider and weigh these issues on the basis of practical considerations during the design phase comprehensively. As the technology develops and progresses further, the applications expand, the privacy protection systems built using AI & blockchain will draw more attention in the upcoming future. On the basis of research findings, technical approaches, and application scenarios, they can be classified into three categories.
- Privacy protection method application in the IoT or Internet of Things industry by utilizing both blockchain and AI technology.
- Privacy protection method application in smart contract and services that make use of both blockchain and AI technology.
- Large-scale data analysis methods that offer privacy protection by utilizing both blockchain and AI technology.
The technologies belonging to the first category focus on the implementation of AI and blockchain technologies for privacy protection in the IoT industry. These methods use AI techniques to analyze high volumes of data while taking advantage of decentralized & immutable features of the blockchain network to ensure authenticity and security of the data.
The technologies falling in the second category focus on fusing AI & Blockchain technologies for enhanced privacy protection by making use of blockchain’s smart contract & services. These methods combine data analysis and data processing with AI and use blockchain technology alongside to reduce dependency on trusted third parties, and record transactions.
Finally, the technologies falling in the third category focus on harnessing the power of AI and blockchain technology to achieve enhanced privacy protection in large-scale data analytics. These methods aim to exploit blockchain’s decentralization, and immutability properties that ensure the authenticity & security of data while AI techniques ensure the accuracy of data analysis.
Conclusion
In this article, we have talked about how AI and Blockchain technologies can be used in sync with each other to enhance the applications of privacy protection technologies by talking about their related methodologies, and evaluating the five primary characteristics of these privacy protection technologies. Furthermore, we have also talked about the existing limitations of the current systems. There are certain challenges in the field of privacy protection technologies built upon blockchain and AI that still need to be addressed like how to strike a balance between data sharing, and privacy preservation. The research on how to effectively merge the capabilities of AI and Blockchain techniques is going on, and here are several other ways that can be used to integrate other techniques.
Edge computing aims to achieve decentralization by leveraging the power of edge & IoT devices to process private & sensitive user data. Because AI processing makes it mandatory to use substantial computing resources, using edge computing methods can enable the distribution of computational tasks to edge devices for processing instead of migrating the data to cloud services, or data servers. Since the data is processed much nearer the edge device itself, the latency time is reduced significantly, and so is the network congestion that enhances the speed & performance of the system.
Multi-chain mechanisms have the potential to resolve single-chain blockchain storage, and performance issues, therefore boosting the scalability of the system. The integration of multi-chain mechanisms facilitates distinct attributes & privacy-levels based data classification, therefore improving storage capabilities and security of privacy protection systems.
Credit: Source link